Table of Contents
- Introduction----------------------3
- Requirement analysis-------------3
- Network design-------------------6
- Critical analysis 750--------------8
- Constraints and limitations-------10
- Conclusion-----------------------11
- Reference------------------------12
Introduction
The wireless network is one kind of computer network that utilized wireless data connections between nodes for ensuring wireless connectivity within a range. In this report, a wireless network will be created for a client company Mahnoor Solutions. The client has 100 employees spread across 9 floors who require connectivity for their endpoints on all those floors. Therefore, in this report, a requirement analysis will be performed to identify the functional as well as non-functional requirement of the client company. Based on the outcome of the requirement analysis, a wireless network design will be created for the organization that will provide wireless connectivity through the building of the client.
The report will discuss the placement of wireless antennas so that user will get highest signal quality. Furthermore, a critical analysis will be performed regarding the design of the network, placement of network device, Wi-Fi channel utilized, and selection for networking devices. Finally, some constraints and limitations of the designed wireless network will be analysed in this report. Moreover, the network will be designed in such a way that the users can access internet and communicate from different floors without any problem.
Requirement analysis
To design and implement a secure wireless network solution for the client company, it is vital to perform a comprehensive analysis of the requirements and needs of the company. This analysis will help to understand the unique demands and limitations of the client organization and try to suggest the best and most efficient network design. In order to meet the requirements of the client company, the first priority is to establish uninterrupted wireless coverage throughout all floors of the building. With a total of nine floors, it becomes important to deliver reliable connectivity in every area of the building, including the area of offices, common spaces, and even meeting rooms [12]. The main goal of this new wireless network solution will be to ensure that any individual within the coverage area can access the wireless network seamlessly regardless of their location within the building.
The second main consideration in the process of designing the wireless network is its ability to support the expected number of users simultaneously. As there are 100 employees working in the client organization, it becomes crucial to ensure that designing the network should be done in such a manner that it can handle the user capacity without facing any issues of performance degradation and congestion in the delivered network. By carefully analyzing the anticipated user load and implementing suitable network design principles, the new wireless network can swiftly meet the current user’s demands while also allowing space for future expansions without compromising the experiences of users or the performance of the network [10].
Another key aspect of a network design is maintaining a satisfactory signal quality for indoor users is of utmost importance. To achieve this, careful consideration must be given to the strategic placement of access points throughout the building [14]. This approach enables users to seamlessly connect to the wireless network and enjoy a reliable and consistent signal, enhancing their overall experience and productivity within the premises. Last but not least, the effective mitigation of interference is also important to optimize the performance of the wireless network. It is important to make careful considerations while selecting the most suitable Wi-Fi channels which can help to minimize the interference from the nearby devices and other networks [11].
Hardware requirement
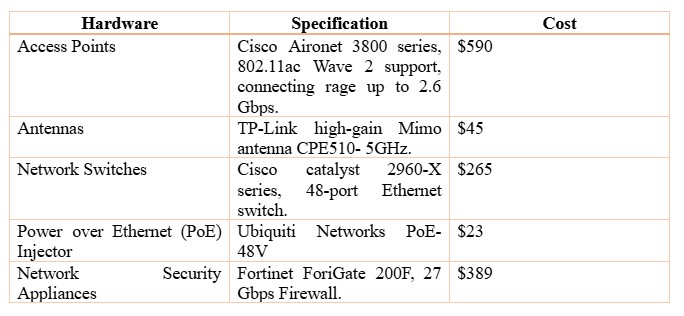
Non-functional Requirements
In addition to hardware requirements, there are some non-functional requirements that should also be considered while designing a wireless network.
- Security:To ensure the confidentiality and integrity of sensitive data and secure communication, the network should integrate robust security measures. This could encompass the incorporation of encryption protocols, strong authentication mechanisms, and access controls to prevent unauthorized access to the network, the integration of these security measures, the wireless network can create a secure environment, safeguarding against potential security breaches and ensuring that sensitive data remains protected from unauthorized access or tampering.
- Reliability:To minimize downtime and disruptions to client operations, the wireless network should provide a high level of reliability and uptime. It is essential to incorporate redundancy measures such as backup power supplies and failover mechanisms to guarantee continuous network availability. By integrating these redundancy measures, the wireless network can guarantee continuous availability and provide a reliable communication infrastructure for the client, reducing the risk of operational interruptions and maintaining a consistent and dependable connectivity experience.
- Scalability:The network design should possess scalability to adapt to future growth and evolving organizational needs. It must have the capability to accommodate additional users, devices, and network traffic without experiencing significant performance degradation. By incorporating scalable elements into the network design, such as scalable hardware and infrastructure, the network can easily adapt to changing demands and ensure consistent performance even with increased usage. This scalability feature is essential for future-proofing the network and providing a sustainable solution that can meet the organization's evolving requirements over time.
- Performance:To meet the requirements of the client company, the wireless network should consistently provide reliable performance. This contains delivering low latency, minimal packet loss, and high throughput, which are important for supporting bandwidth-intensive applications and ensuring seamless user experiences. The network should be capable of handling the demands of data-intensive tasks, such as streaming, video conferencing, and large file transfers, without compromising performance. By prioritizing performance optimization techniques, such as efficient network protocols, quality of service (QoS) mechanisms, and intelligent traffic management, the wireless network can consistently deliver the necessary performance levels to meet the client company's requirements and support their business operations effectively.
Network design
From the requirement analysis, it has been identified that the client has 100 employees spread across 9 floors who require connectivity for their endpoints on all those floors. To meet the requirements, it is proposed to the wireless network using a controller-based architecture. It is also has been recommend using access points that support the latest Wi-Fi 6 standard and offer features such as beamforming and MU-MIMO to enhance the signal quality and throughput [3]. The access points will be distributed evenly across all the floors to provide seamless coverage. The network design for the client company is shown below:
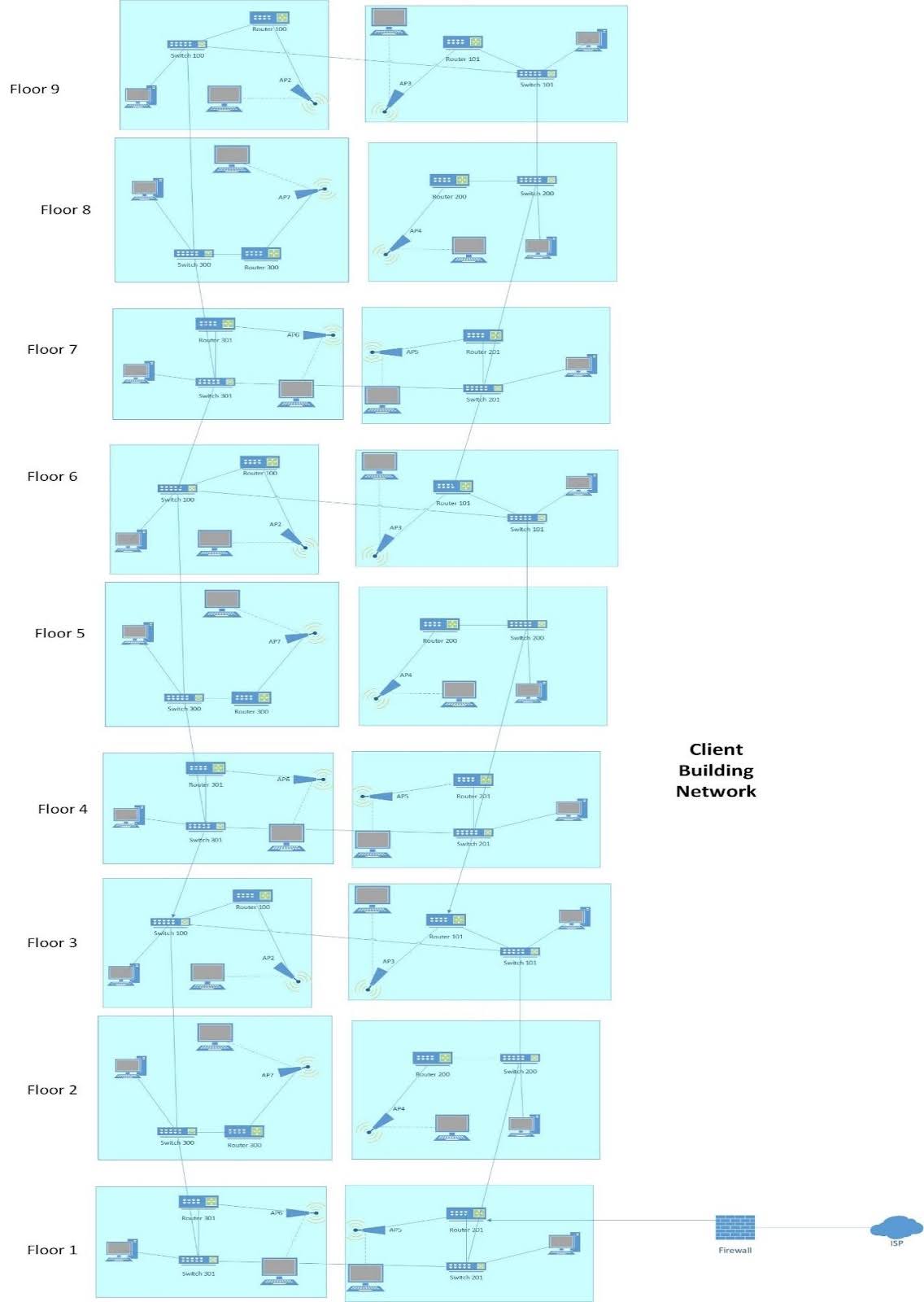
------------Figure: Network Diagram------------
From the above figure, it can be seen that wireless access point has been placed in all 9 floor of the client company to provide better network connectivity. Some of the access points has been placed near the center of each floor, preferably in a location where there are no obstructions such as walls or furniture that could interfere with the signal. However, some of the access point has been placed near high-traffic areas such as entrances, hallways, and common areas to ensure that users can connect even in areas with heavy usage [3]. In each floor two access point has been placed to ensure high coverage while minimizing the interference. The wireless points also has been placed in both 2.4 and 5 GHz channel.
Along with the wireless connectivity, security considerations of the client company also has been considered. For network security, each wireless access point has been password-protected. To ensure that only authorised users and client company personnel will use the organization’s wireless network, authentication and authorization settings have been applied to every access point. For security purposes, firewall has been placed within the internet and main router. In order to guarantee that the network is always accessible, network failover has been enabled. The network's redundancy has been ensured by constructing a redundant link between the various buildings. Because of this, the network at the client company has been designed such that no staff members would encounter any delays while switching between locations [1]. The user may effortlessly wander between several buildings and utilise wireless devices with fast internet.
Critical analysis
As per [8], wireless communication has become increasingly popular in recent years due to its convenience and flexibility. The proposed wireless network for the client aims to provide seamless connectivity across all nine floors to meet the needs of 100 employees. To ensure client management, monitoring, and configuration of the wireless network, a controller-based architecture has been recommended. In this architecture, all access points are centrally controlled by a dedicated controller. Implementing access points that support the latest Wi-Fi 6 standard is highly recommended as it offers numerous advantages such as higher data rates, reduced latency, and improved coverage when compared to previous Wi-Fi standards. Along with also incorporating features like beam forming and MU-MIMO (multi-user-multi-input-multi-output) enhances the signal quality and increases throughput.
According to [5], in an attempt to provide seamless coverage, the access points have been distributed evenly across all floors. Strategic placement of access points near the center of each floor ensures minimal interference from obstructions like walls and furniture. Moreover deploying access points in high-traffic areas such as entrances, hallways, and common areas guarantees connectivity even in heavily utilized zones. For optional coverage and interference reduction, two access points have been positioned on each floor. By deploying access points in both the 2.4 and 5 GHz channels, great flexibility is provided to connect devices operating in different frequency ranges. Ensuring network security is a top priority for the client company. To prevent unauthorized access, each wireless access point is password protected. Authentication and authorization setting is being applied to every access point allowing only authorized users and client company personnel to connect to the network. A firewall has been implemented within the internet and maintained to provide an extra layer of security. network failover has also been enabled to guarantee continuous network accessibility. To ensure network redundancy, a redundant link has been established between the various buildings. This design ensures uninterrupted connectivity for staff members switching between locations.
As per [4], the proposed wireless network also possesses certain limitations that need to be considered. One key limitation is the coverage area of each access point, which may result in dead zones in certain areas. These dead zones can occur due to physical obstacles like walls, furniture, or other electronic devices that interfere with the wireless signal. To mitigate this issue, access points can be repositioned or additional access points can be added to improve coverage in these areas. Another limitation is the susceptibility of the wireless network to interference from neighboring wireless networks or electronic devices operating on the same frequency. Such interference can degrade the signal quality and reduce network throughput. To address this concern, access points can be configured to utilize different channels or frequencies, and regular monitoring of the network for potential interference should be conducted. The security of the wireless network is another crucial aspect to consider. While authentication and authorization settings have been implemented, unauthorized access to the network is still a possibility. Weak passwords or security vulnerabilities in the access points and other network devices can be exploited by malicious actors. To counter this, regular security audits and timely updates to the network devices should be conducted ensuring that the network remains secure and resilient.
According to [6], to bolster network security, a firewall is deployed within the internet and the main router. This serves as a proactive barrier, filtering incoming and outgoing traffic based on predefined network security policies. The firewall’s role is to identify and block any potentially malicious or unauthorized users from gaining access to sensitive information ultimately, safeguarding the network from external threats. Along with it the network failure mechanisms are enabled to ensure continuous network accessibility. In the event of a network failure or disruption failover mechanisms redirect network traffic through alternative paths or backup connections minimizing downtime and guaranteeing uninterrupted connectivity to a lot of employees. Therefore, the proposed network design showcases a well-thought-out approach to meet the connectivity needs of the client company’s 100 employees spread across nine floors. The utilization of controller-based architecture, Wi-Fi 6 standard access points, and strategic placement of devices demonstrates a commitment to delivering seamless coverage and enhance performance. However, the limitations related to coverage, interference, and security should be addressed through proactive measures such as repositioning access points, monitoring interference levels, and implementing robust security protocols. By continuously adapting, and refining the network design, the client company can establish a robust future-proof wireless infrastructure that supports its evolving connectivity requirement.
Constraints and limitations
- Coverage limitations: The coverage area of each access point may be limited, leading to potential dead zones or areas with weak signal strength. Physical obstructions such as walls, furniture, or electronic devices can interfere with signal propagation, impacting the coverage range. Addressing coverage limitations may require repositioning access points or adding new access points in specific areas.
- Interference Susceptibility: The wireless network is vulnerable to interference from neighboring wireless networks or electronic devices operating on the same frequency. Interference can degrade signal quality, leading to reduce throughput and potential connectivity issues [9]. Regular monitoring of interference levels and adjustments of the access point configuration to different channels or frequencies help mitigate this limitation.
- Security Vulnerability: Despite authorization and authentication settings, unauthorized users may still gain access to the network due to weak passwords or security vulnerabilities. Regular security audits and updates to network devices are necessary to ensure the network remains secure and protected against network breaches.
- Scalability Challenges: The proposed network design may face scalability challenges when accommodating an increasing number of devices or expanding the network infrastructure. Additional access points and network resources may be required to maintain optimal performance and coverage as the number of users and devices grows.
- Limited Bandwidth: The available bandwidth is shared among connected devices and as the number of users increases the available bandwidth per user decreases, potentially impacting network performance [7]. Bandwidth network techniques such as Quality of Service (QoS) policies, can help prioritize critical applications and ensure equitable bandwidth distribution.
Conclusion
The complete report is based on providing the best design and implementation of strong and secure wireless networking solutions for the client’s building. A comprehensive requirement analysis has identified key aspects that have been addressed in the provided network design. The report has focused on providing seamless coverage to everyone within the building, accommodating the 100 employees across the nine different floors. The new network design also focuses on ensuring acceptable signal quality for indoor users by strategically placing the antennas in the correct locations and entrances. Which will help to deliver optimal coverage and signal strength throughout the building. Another significant consideration is mitigating interference from nearby users. It is essential to select appropriate Wi-Fi channels, opting for those with less congestion. By identifying and utilizing the least crowded channels, interference can be minimized, leading to improved network performance. By implementing these factors into the network design and following the proposed plan client can get the benefits of a secure and reliable wireless network that fulfills their connectivity requirements in every aspect. The design ensures optimal coverage, signal quality, and channel selection, resulting in a seamless wireless experience for the organization's employees across all floors.
Reference
- [1] Wang, C.X., Di Renzo, M., Stanczak, S., Wang, S. and Larsson, E.G., 2020. Artificial intelligence enabled wireless networking for 5G and beyond: Recent advances and future challenges. IEEE Wireless Communications, 27(1), pp.16-23.
- [2] Letaief, K.B., Chen, W., Shi, Y., Zhang, J. and Zhang, Y.J.A., 2019. The roadmap to 6G: AI empowered wireless networks. IEEE communications magazine, 57(8), pp.84-90.
- [3] Dajer, M., Ma, Z., Piazzi, L., Prasad, N., Qi, X.F., Sheen, B., Yang, J. and Yue, G., 2022. Reconfigurable intelligent surface: Design the channel–A new opportunity for future wireless networks. Digital Communications and Networks, 8(2), pp.87-104.
- [4] Zappone, A., Di Renzo, M. and Debbah, M., 2019. Wireless networks design in the era of deep learning: Model-based, AI-based, or both?. IEEE Transactions on Communications, 67(10), pp.7331-7376.
- [5] Wang, C.X., Di Renzo, M., Stanczak, S., Wang, S. and Larsson, E.G., 2020. Artificial intelligence enabled wireless networking for 5G and beyond: Recent advances and future challenges. IEEE Wireless Communications, 27(1), pp.16-23.
- [6] Muhambe, T.M. and Omumbo, C.M.R.N.J., 2021. Evaluation of Routing Performance using OSPF and Multi-Controller Based Network Architecture.
- [7] Khorov, E., Levitsky, I. and Akyildiz, I.F., 2020. Current status and directions of IEEE 802.11 be, the future Wi-Fi 7. IEEE access, 8, pp.88664-88688.
- [8] Oughton, E.J., Lehr, W., Katsaros, K., Selinis, I., Bubley, D. and Kusuma, J., 2021. Revisiting wireless internet connectivity: 5G vs Wi-Fi 6. Telecommunications Policy, 45(5), p.102127.
- [9] Dolan, E. and Widayanti, R., 2022. Implementation of authentication systems on hotspot network users to improve computer network security. International Journal of Cyber and IT Service Management, 2(1), pp.88-94.
- [10] Almohamad, A., Tahir, A.M., Al-Kababji, A., Furqan, H.M., Khattab, T., Hasna, M.O. and Arslan, H., 2020. Smart and secure wireless communications via reflecting intelligent surfaces: A short survey. IEEE Open Journal of the Communications Society, 1, pp.1442-1456.
- [11] George, E.M. and Jacob, L., 2020. Interference mitigation for coexisting wireless body area networks: Distributed learning solutions. IEEE Access, 8, pp.24209-24218.
- [12] Singh, A., Sharma, S. and Singh, J., 2021. Nature-inspired algorithms for wireless sensor networks: A comprehensive survey. Computer Science Review, 39, p.100342.
- [13] Porambage, P., Gür, G., Osorio, D.P.M., Livanage, M. and Ylianttila, M., 2021, June. 6G security challenges and potential solutions. In 2021 Joint European Conference on Networks and Communications & 6G Summit (EuCNC/6G Summit) (pp. 622-627). IEEE.
- [14] Jeremiah Ekah, U., Iloke, J., Obi, E. and Ewona, I., 2022. Measurement and performance analysis of signal-to-interference ratio in wireless networks. Asian Journal of Advanced Research and Reports, 16(3), pp.22-31.

