Instructions on Assessment:
This assignment constitutes 70% towards the final mark for this module. Any queries relating to this assignment should be discussed with the module tutor. This is an INDIVIDUAL piece of work contributing to the module assessment. Deliverables should be assembled into a single report document, which includes (critical appraisal, research, and snapshot evidence of tasks carried out and justification of technologies used). Submission will be in the form of an MS Word report (3000 words).
Brief:
This is an individual assignment. This task weights 70% of the overall grade.
For this coursework, you are required to implement network security. You must reflect/validate the network security services and produce an associated 3000 words report. You need to complete this assignment as an individual. Please provide a detailed walk-through snippet of secure network and services. The quality of walk-through snippet will influence the weighting of assignment marks.
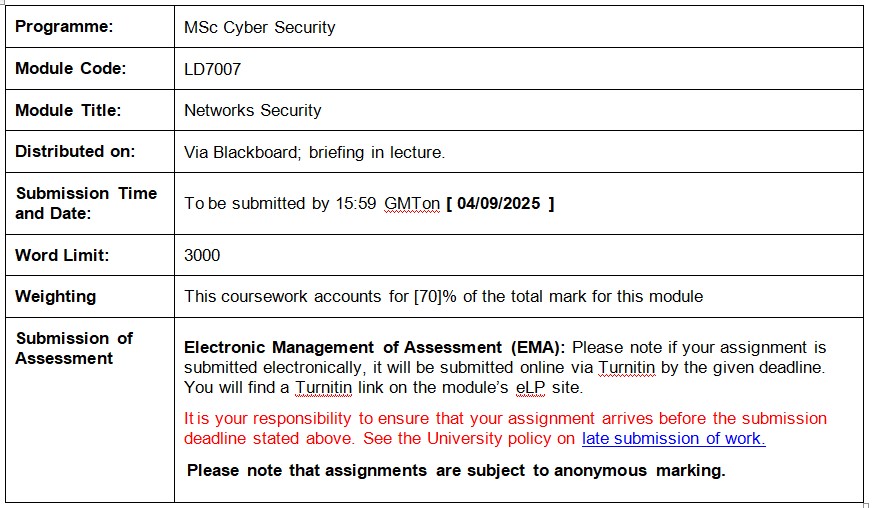
Origin Bank was vulnerable in terms of its network system. IT engineers conducted penetration tests on the network system, yet they were unable to detect any vulnerabilities. However, certain protocols such as POP3 and ICMP were enabled on the external network, and weak passwords were identified. Consequently, the organization is now prioritizing the implementation of robust network security measures to safeguard confidential data during transmission. This initiative is also intended to facilitate security auditsYou have been asked to implement and test the network security measures for OriginBank. The network topology is outlined on the next page.
Your main task is to design and implement network security with direct link to Internet/Wide Area Network (WAN) in a series of Block Tasks. You should be able to design and implement Site-to-Site VPN Tunnel, ACL and IOS based Intrusion Prevention System (IPS) along with basic device hardenings to secure organisation Local Area Network (LAN) using appropriate network simulation environment. The organisational network enable integration with IPsec VPN that allow strong encryption to ensure confidentiality and integrity. The network and security services can be designed using well known network simulators.
Your work must be presented in the form of a Project Report and be no longer than 3000 words (excl. references, figures, tables, and appendices) plus a facing page that includes the executive summary. This should be typed on A4 paper and use a font size Arial 11 single spacing. For completeness, you may if you wish include additional material in an appendix but this will not contribute to the marks.
Section 1: Block A: Network Architecture and Communication [30 marks]
(suggested word limit for this section is 800 words)
- • Only DNS and HTTP traffic is allowed from Internet hosts destined for the DMZ
- • Allow HQ office to access the Internet (Public DNS/Web server) and traffic from the Internet is not allowed into the internal network unless it is in response to a request that originated from within the internal network.
- • Allow both traffic from both LANs in BorderRouter (HQ) and Branch Router to go through VPN tunnel.
1. Implement basic device hardening with the following services fully running and functional, DNS Server, Web Server and Sys log Server.
2. Allocate and distribute the IP addresses to network and end devices according to the given design both static configuration and dynamic configuration via DHCP server.
3. Configure to allow internal network traffic to access the Internet. Implement and configure Dynamic Routing using RIPV2/OSPF protocol to demonstrate effective routing on WAN network between internal and external site. It is preferred to use OSPF.
4. Configuring appropriate VLAN trunking for multiple VLAN’S to segment the traffic in separate broadcast domains for security reasons.
5. Design and implement fully functional Inter-Vlan routing using IEEE 802.1Q encapsulation standard to demonstrate connectivity between business sites.
Section 2: Block B: Secure Operations and Service Delivery [30 marks]
(suggested word limit for this section is 800 words)
1. Configure Access Control List (ACL) on the routing device to implement the Security Policy to restrict the network access according to the organisation policy. (Reasonable assumptions can be made).
2. Configure an SSH server and Configure AAA for console line and vty lines access authentication.
3. Configure the HQ (border router) to Implement and configure a Site-to-Site IPsec VPN to comprehensively encrypt the traffic traveling over WAN network between internal and external site networks. Evidence must be provided on how the VPN Tunnel provides integrity and confidentiality for the IP packets traversing in and out of the network.
4. Implement IOS based Network Intrusion Prevention System (IPS) and test its efficiency in your deployment to secure internal network.
Implement a firewall and configure relevant rules in the context of the given scenario. Evidence the functionality and provide a narrative elaborating on the rationale behind the location on the network.
Section 3: Block C: Research & Development [40 marks]
(suggested word limit for this section is 1400 words)
1. Zero Trust is a network security model, based on a strict identity verification process. The framework dictates that only authenticated and authorized users and devices can access applications and data. At the same time, it protects those applications and users from advanced threats on the Internet. Considering the context of the case study and practical implementation of block A and B, please discuss and critically analyse the Zero Trust Network Security Model. You should refer to your security implementation in a given network for the sake of discussion and back up your findings with credible references to demonstrate critical research on the topic.
2. With reference to the case study, critically discuss how IPsec VPN can be used to achieve security. Identify the level of reliability and critically discuss the cryptographic mechanism of IPsec.
Deliverable(s)
Create a single report for each of the three (3) block tasks described in the previous section. You should record and analyse all the steps followed to complete the installation configuration of network security services. Although a certain flexibility of the way you construct your report, an indicative structure is given below:
Report Structure:
1. Executive Summary
2. Block A: Architecture and Communication
2.1 Configure IP connectivity and device hardening
2.2 Configure servers DNS, WEB, SYS-Log
2.3 Configure Dynamic Routing (RIPV2) and Inter-Vlan Routing/Trunking
3. Block B: Secure Operations and Service Delivery
3.1 Implement ACL on Routing device
3.2 Configure an SSH and Configure AAA
3.3 Implement Site-To-Site IPSec VPN
3.4 NIPS implementation and testing
3.4 NIPS implementation and testing
3.5 Firewall configurations
4. Research & Development
4.1 Zero Trust Network Security Framework
4.2 Overview of VPN reliability
4.3 Cryptographic mechanism of IPSec
5. Conclusion and Future Work
Mapping to Programme Goals and Objectives
The following learning outcomes will be assessed by this assignment:
1. Develop an in-depth understanding of fundamental concepts and challenges in data and network security
2. Demonstrate concepts related to basic cryptography
3. Critically evaluate threats to data and network security; design and implement security solutions using networking IOS
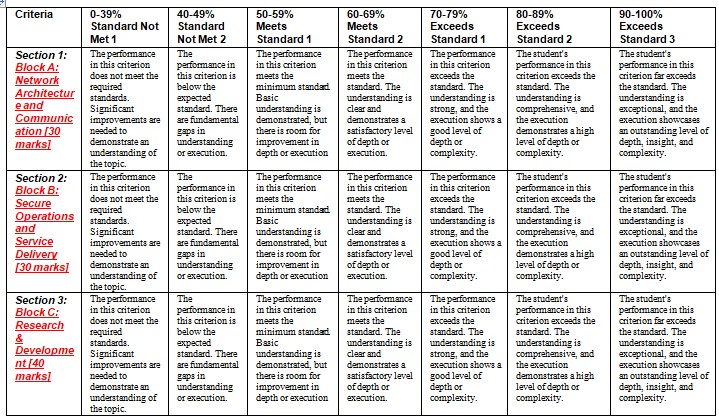
Module Specific Assessment Criteria and Rubric
ASSESSMENT REGULATIONS
You are advised to read the guidance for students regarding assessment policies. They are available online here.
Academic Misconduct
The Assessment Regulations for Taught Awards (ARTA) contain the Regulations and procedures applying to cheating, plagiarism,the use of Artificial Intelligence (AI) Systems, and other forms of academic misconduct
The full policy is availablehere
You are reminded that plagiarism, collusion,the use of Artificial Intelligence (AI) Systems, and other forms of academic misconduct, as referred to in the Academic Misconduct procedure of the assessment regulations, are taken very seriously. Assignments in which evidence of plagiarism or other forms of academic misconduct is found may receive a mark of zero.
Late submission of work
Where coursework is submitted without approval, after the published hand-in deadline, the following penalties will apply.For coursework submitted up to 1 working day (24 hours) after the published hand-in deadline without approval, 10% of the total marks available for the assessment (i.e.100%) shall be deducted from the assessment mark.
For clarity: a late piece of work that would have scored 65%, 55% or 45% had it been handed in on time will be awarded 55%, 45% or 35% respectively as 10% of the total available marks will have been deducted.
The Penalty does not apply to Pass/Fail Modules, i.e. there will be no penalty for late submission if assessments on Pass/Fail are submitted up to 1 working day (24 hours) afterthe published hand-in deadline.
Coursework submitted more than 1 day (24 hours) after the published hand-in deadline without approval will be marked as zero but will be eligible for referral. The reassessment should where appropriate, and as determined by the Module Leader, be the same method (e.g. essay) but maybe with a different task (e.g. different essay title) or with the same task (e.g. the same essay title) as indicated in the Module handbook.
In modules where there is more than one assessment component, Students are not required to complete all assessment components if an overall Pass Mark (40% UG, 50% PGT) has been achieved.
The only permitted exception will be in cases where the University is prevented from doing so by a PSRB requirement. In the case of PSRB requirements, a variation order will be required from the regulations.
In modules, where there is more than one assessment component and an overall pass mark has not been achieved, Students will be eligible for a referral* in the individual failed module and/or not attempted component(s) of assessment.
These provisions apply to all assessments, including those assessed on a Pass/Fail basis.
The full policy can be found here
Word limits
The word count is to be declared on the front page of your assignment and the assignment cover sheet. The word count does not include appendices, glossary, footnotes, tables and references.
Please note, in text citations [e.g. (Smith, 2011)] and direct secondary quotations [e.g. “dib-dab nonsense analysis” (Smith, 2011 p.123)] are INCLUDED in the word count.
If this word count is falsified, students are reminded that under ARTA this will be regarded as academic misconduct.
For those assessments where students are required to keep to the word limit, it is proposed that they should be informed that the marker will stop reading at the point when they judge that the word limit exceeds the recommended word count by more than 10%. The marker will indicate the point at which they stop reading on the text.
Students must retain an electronic copy of this assignment (including ALL appendices) and it must be made available within 24hours of them requesting it be submitted.
The full Word Limit Policy is available here.

